The digital marketing landscape is evolving at a rapid pace. With data-driven strategies, marketers now have access to consumer information. But, this also amplifies the need for stringent data protection to build customer trust and follow regulations.
In today’s rapidly evolving digital marketing landscape, data masking has become a crucial technique for marketers to strike a balance between data utility and privacy.
Contents
What is Data Masking?

Data masking refers to the process of obscuring or altering original sensitive data with fictitious information that maintains the format and structure of the original data. It substitutes real data with fake but realistic-looking data.
This practice enables organizations to provide broader access to non-sensitive information for purposes such as testing, development, and troubleshooting, all while maintaining security. At the same time, it ensures that confidential data remains protected. There are various data masking techniques and methodologies:
Tokenization
Tokenization operates by substituting sensitive data with unique symbols or tokens that retain the format and structure while concealing the actual values. A token vault stores the relationship between the token and the original data. This allows accurate analytics without exposing real data. It offers better performance and scalability than encryption for large-scale deployments.
Encryption
Encryption encodes original data into ciphertext rendered indecipherable without the cryptographic key. It provides a high level of protection but requires key management processes. Format-preserving encryption retains data patterns for usability even in encrypted form. Partial or selective encryption reduces overhead. Encryption provides robust protection but requires balancing usability.
Shuffling
Shuffling mixes up parts of the data fields or records while keeping specific identifiers intact. This preserves utility, especially for purposes like testing while masking sensitive elements. For instance, customer account numbers can shuffle while retaining customer names. Constraint-based shuffling can maintain relationships between records by shuffling linked fields. Shuffling provides variable protection levels based on implementation complexity.
Data Anonymization
Data anonymization involves methods such as blurring, masking, changing, and combining that could lead back to specific people. This creates data that looks real but isn’t, keeping important patterns without revealing personal info or sensitive details. Anonymization provides strong privacy protection but can impact analytics if taken to extremes. Hybrid implementations balance utility with lower re-identification risks.
With regulations like GDPR and CCPA mandating more stringent privacy requirements, data masking provides a mechanism for digital marketers to tap into the wealth of consumer data analytics while ensuring full compliance with legal obligations.
Compliance and Regulatory Landscape
With rising awareness around data protection exemplified by EU citizens having heard about GDPR on digital marketing, digital marketers must align strategies with evolving regulations. For instance, GDPR requirements include:
- Requiring opt-in consent from customers for data collection and processing
- Mandating data breach notification within 72 hours
- Stipulating privacy by design and default for all processes and systems
- Granting customers the right to access their data and requiring entities to provide it in a simple format
The stiff penalties for non-compliance under GDPR and CCPA, which range from 2,500 to 7,500 dollars per violation, underscore the criticality of data safeguards like masking to avoid hefty fines. Embedding privacy into processes allows marketers to steer clear of continuously growing regulatory obligations.
Challenges in Implementing Data Masking
Organizations encounter challenges when implementing data masking due to integration difficulties. Some key obstacles include
- Siloed Data: Data spread across different departments prevents the unified view needed for effective masking.
- Legacy Systems: Outdated systems may not support advanced data masking and protection.
- Resource Constraints: Many companies, especially SMBs, are limited in budget, time, and expertise for adopting data masking.
- Data Quality Issues: Poor quality data, with errors, makes accurate masking challenging.
However, overcoming these initial challenges is crucial, considering that data breaches typically take an average of 280 days to identify and address. Overcoming these hurdles sets the stage for long-term success in data protection
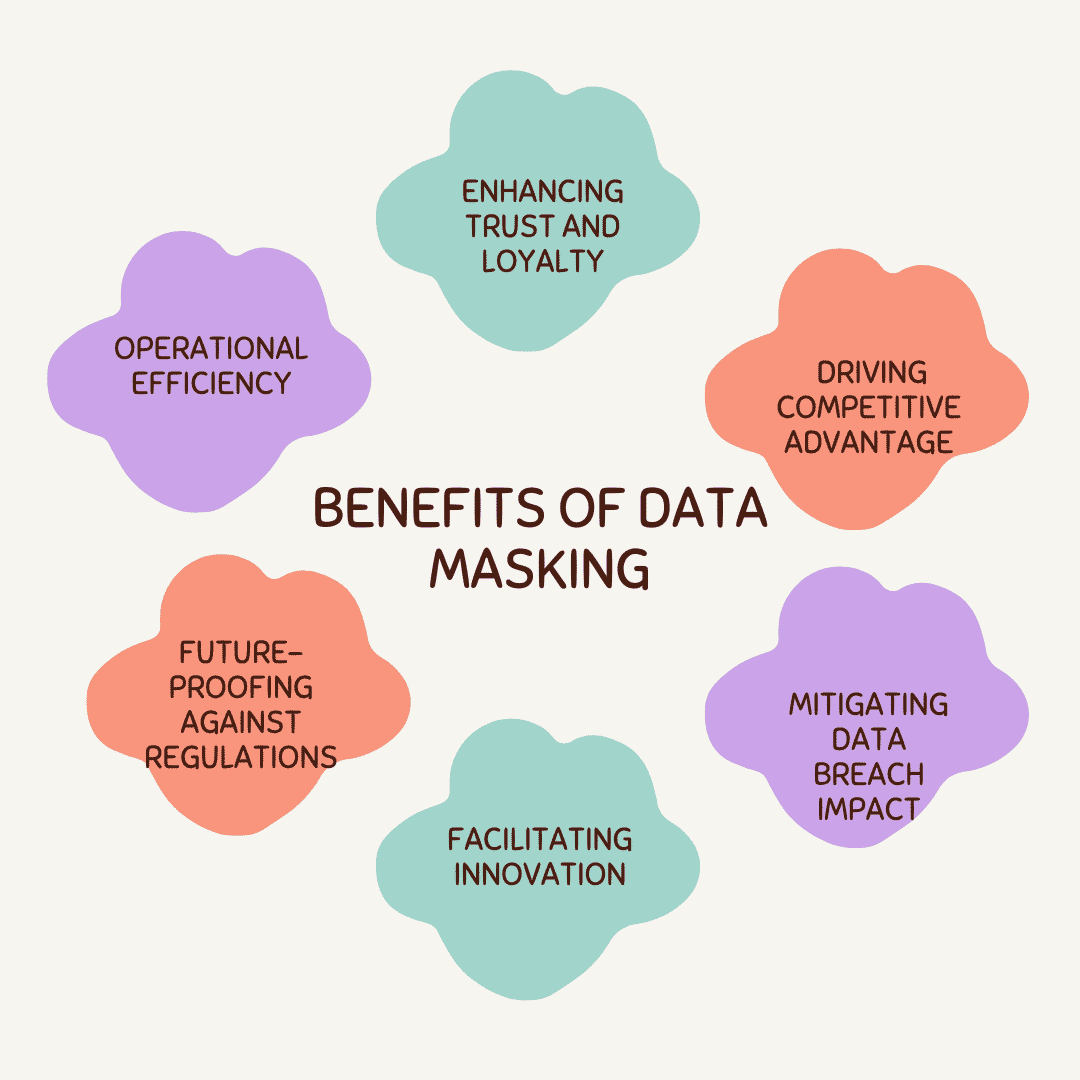
Benefits of Data Masking in Digital Marketing
Data masking allows digital marketers to get into the wealth of consumer data analytics while comforting 92% of consumers worried about privacy issues. The enhanced customer trust and risk reduction also result in a 2.7 times ROI on average, as per Forrester. Some key advantages include:
- Enhancing Trust and Loyalty – Assuring customers their data builds brand reputation and loyalty.
- Future-proofing Against Regulations – Proactive masking ensures compliance with evolving privacy regulations.
- Minimizing Data Breach Impact – Masking limits damage from breaches as original data remains protected.
- Facilitating Innovation – Wider data access for development/testing without compromising privacy accelerates new products and features.
Therefore, data masking provides digital marketers with a competitive advantage by ensuring robust data protection and privacy assurance.
Best Practices for Effective Data Masking
Conduct a data classification assessment: Catalog all data assets and classify them based on their sensitivity levels. This allows for optimal policies to be defined for each data type.
Adopt a risk-based approach: Prioritize masking for high-risk data, such as intellectual property, customer data, and financial information.
Select appropriate masking techniques: Choose masking methods like substitution, shuffling, encryption, etc. based on data type, utility requirements, and security needs.
Test extensively before deployment: Validate that masked data retains utility for downstream analytics and operations through rigorous testing.
Automate processes wherever possible: Automated masking integration minimizes errors and resource overhead for ongoing maintenance.
Mask data at the source: Masking data as close to the point of capture improves security and performance.
Monitor data access and compliance: Continuously monitor masking effectiveness, data leaks, and compliance with policies.
Retain original data securely: Store original unmasked data securely with tightly controlled access for reverting if necessary.
Update strategies periodically: Ensure masking policies evolve to address new regulations, threats, and data types.
Document policies and train personnel: Educate all stakeholders on masking best practices to maintain data integrity.
Case Studies and Success Stories
The real-world impact of effective data masking strategies is evident in examples such as:
- Starbucks reduced data exposure risks by a certain percentage through masking to protect customer information.
- Salesforce leveraging masking to improve privacy and compliance across cloud platforms, enhancing trust.
- UC Berkeley’s masking solutions aid in compliance and reduce breach risks based on its specific requirements.
Future Trends and Predictions
Data masking adoption will intensify with regulations covering 65% of the global population by 2023 as per Gartner. IDC predicts global privacy spending to reach 44 billion dollars by 2024. Emerging technologies are also expected to enhance data masking capabilities:
AI and ML
Artificial intelligence and machine learning will enable more automated, nuanced, and proactive data masking capabilities. These technologies can analyze vast datasets to classify information based on sensitivity levels and recommend optimal masking techniques for each data type. They can also mask data in real-time based on contextual factors like user roles and access permissions.
As threats evolve, predictive algorithms can identify vulnerable data and mask it. Natural language processing can parse unstructured text and apply appropriate masking without compromising semantic meaning. Al and ML will make data masking more adaptive, predictive, and hyper-personalized.
Blockchain
The cryptographic security provided by blockchain technology can enhance data sharing and centralized data masking. Blockchain’s decentralized structure provides greater transparency into how data is used while retaining individual privacy through encryption. Its immutable ledger builds trust by preventing tampering and errors in masking.
Smart contracts can automate data protection policies and permissions, enabling access only to masked data. Overall, blockchain can reduce vulnerabilities in transmitting and storing data for masking, while retaining integrity.
Edge Computing
Edge computing architectures that process data at the source can enable real-time data masking before information is transferred to centralized servers. This overcomes latencies in cloud-based masking.
Computing data at edge devices like sensors, mobiles, and gateways minimizes external exposure of raw unmodified data. It enables decentralized masking that is quick, efficient, and aligned to on-device data context. However, effective coordination between edge and core masking is vital for consistency. Fog computing can play an intermediary role in coordinating multi-layer masking across edge, fog, and cloud.
As consumer awareness and regulations continue to proliferate, robust data protection through masking will become even more pivotal – not just for compliance, but for gaining a competitive advantage by fostering greater customer trust and loyalty while leveraging data.
Conclusion
As digital marketing evolves, data protection and privacy have become crucial issues that brands must now prioritize. Implementing robust data masking strategies is an urgent necessity, not a distant obligation.
Marketers should realize that customer trust and loyalty today depend on transparent data practices and privacy protection. With huge penalties for compliance failures, the risks of inaction far outweigh the costs of proactive protection. By making data masking a core strategic capability rather than a compliance checkbox, marketers can create value in numerous ways.
Despite the challenges, the benefits make data masking capabilities indispensable. As marketing strategies become more data-driven, creating a privacy-first culture is imperative. Integrating masking throughout the data lifecycle lays the groundwork for sustainable innovation and growth fueled by data – which is not only the most valuable asset but also the greatest responsibility for brands today.
Frequently Asked Questions
How does data masking differ from encryption and tokenization?
While data masking, encryption, and tokenization all protect data, masking replaces original data with fakes rather than transforming it. This retains utility for testing and analytics. Encryption scrambles data requiring keys to restore it. Tokenization substitutes data with unique identifiers linked to the original via a token vault.
What are the drawbacks of data masking?
Performance can increase data processing. Masking can introduce data inaccuracies affecting analytics. Complex implementations may be resource-intensive. Custom masking that maintains utility requires expertise.
How can SMBs implement effective data masking?
Start with cost-effective solutions like open-source tools. Focus on high-risk data. Seek expert guidance to avoid pitfalls. Leverage cloud offerings requiring less infrastructure. Emphasize automation for efficiency.
Also Read:
- How to Change Twitch Name Color in Chats & More Tips
- Effective Ways To Improve Your SEO With Heatmaps
- Java Print vs Println – What’s The Difference?
- How to Use Discord in Full-Screen Mode(Web & Application)
- Printf vs cout: What is the difference?